Cybercriminals Are Stealing Marketers’ Leads
Close big loopholes on the web and in email to help prevent phishing, web spoofing and brand impersonation that can lead to stolen leads and lost sales.

Key Points
- With prospects requiring more touches than ever before converting, it’s important to understand the ways cybercriminals can divert marketing leads at the last minute.
- Lost leads are more than wasted marketing budget. They also equal potentially lost sales.
- Phishing, domain spoofing and brand impersonation on social media are among cybercriminals’ lead-stealing tactics.
Depending on the industry, marketers are projected to spend between $31 and $208 per lead in 2021, according to the latest research.[1] And with business-to-business (B2B) leads requiring up to 13 or more touches before they convert, it’s critical that lead-gathering be as frictionless as possible. The last thing a company needs is to do all the work prepping prospects, only to have a cybercriminal swoop in for the “close” by impersonating its brand in a phishing email or spoofed website.
But leads are being hijacked regularly by cybercriminals and sometimes by sneaky competitors. In fact, Mimecast’s recent The State of Brand Protection 2021 (SOBP) report found a 381% spike in brand impersonation attacks against the world’s top 100 most-valuable brands during the first few months of the COVID-19 pandemic last year — and a subsequent new normal of much higher attack levels. To stop such lead stealing before it does too much damage requires proactive monitoring, awareness — and action.
And marketers must stop it: Every lost lead is also a potentially lost sale. Given an average return on investment of $42 for every dollar spent on email marketing,[2] hijacked leads don’t only eat budget, they also eat the sales that some of those leads would have created.
Phishing Emails Are a Direct Threat
The “good” news is, unless you’ve had a security breach, fake phishing emails are not by and large going to your own list of customers. But even a cheaply purchased list is likely to reach some of your customers and prospects. And it only stands to reason that the bigger you are, the more ubiquitous your customer base is and the more likely you’ll fall victim to brand impersonation attacks. What’s more, phishing emails can lead to email deliverability issues because internet service providers attempting to block brand impersonators are likely to also snare legitimate marketing organizations sending email on a brand’s behalf.
In fact, according to the SOBP report, from Oct. 1, 2020, through Jan. 31, 2021, almost every one of Kantar’s top 100 brands were regularly exploited: They averaged more than 715,000 phishing attacks per month, for a total of 2.9 million email phishing attempts during the four-month period.
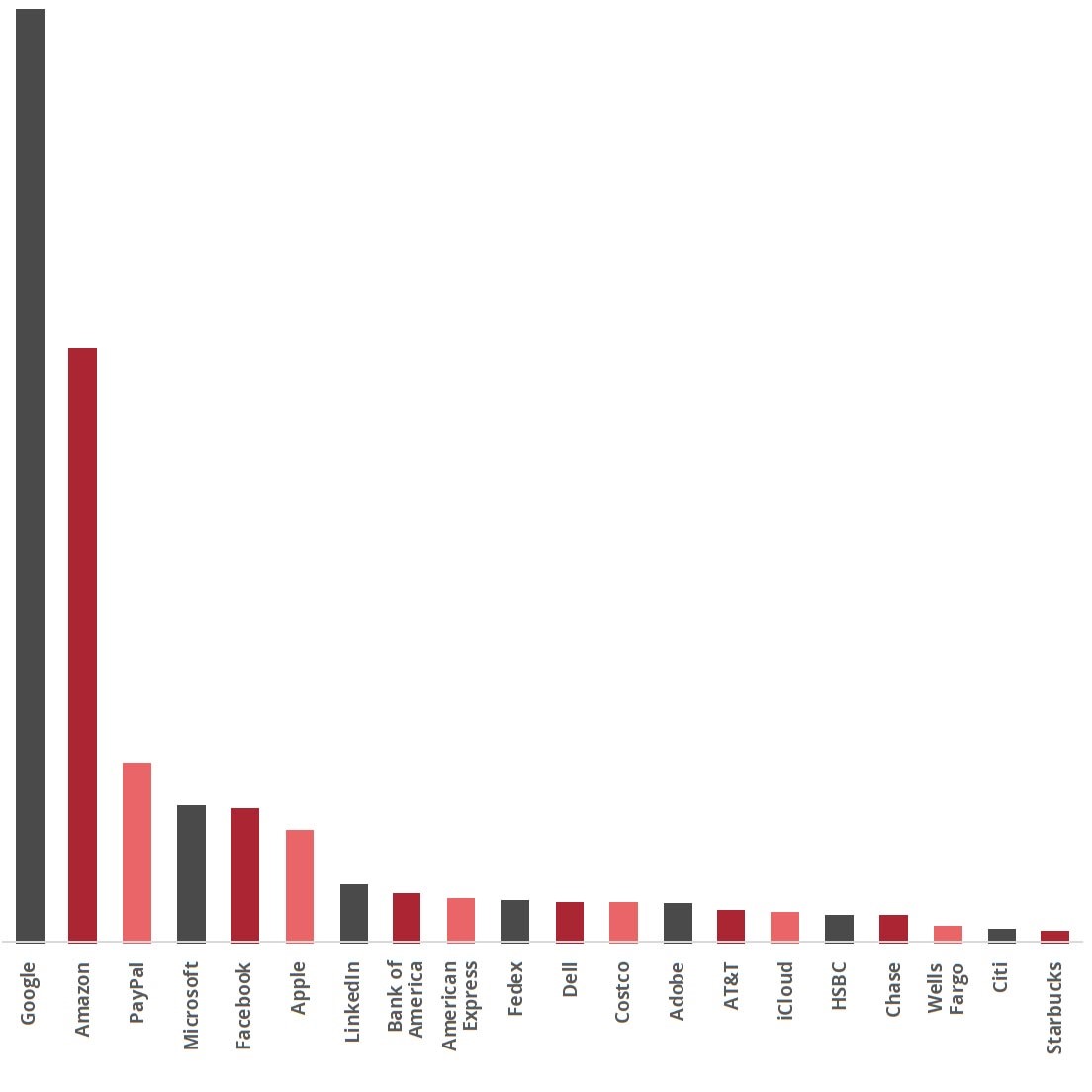
20 most-impersonated of the top 100 brands during the four-month period 10/1/20 — 1/31/21
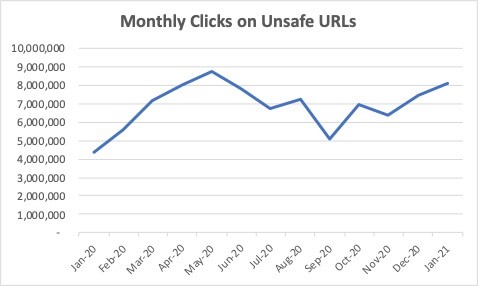
All told, the average monthly number of brand-impersonating emails was sky-high in 2020, at 26.95 million — a 44% increase over the year before, the SOBP report found. Monthly clicks on unsafe URLs doubled from approximately 4 million in January 2020 to approximately 8 million in January 2021. (It’s important to note that the SOBP report is based on an analysis of over 40,000 Mimecast customers who use its email monitoring technology, which means the actual number of fake emails is much higher.)
Actions to take: Awareness is key. Any customer-facing staff (support, sales) should be trained on what to do if a customer or prospect receives a phishing email. Technology can also help protect an organization. For example, DMARC — which stands for Domain-based Message Authentication, Reporting and Conformance — validates that an email is coming from someone authorized to use your domain, and blocks delivery if it isn’t. In addition, machine learning, via a service such as Mimecast’s Brand Exploit Protect web-scanning tool, can help identify attacks in the making, the domains they’re coming from, and automatically block them.
From a communications perspective, if a significant number of phishing emails are detected, consider sending an email blast to your customers so they know you’re on top of the situation. They’ll appreciate hearing about it from you, along with how you’re handling it.
Fraudsters Are Spoofing Your Domain Name
Domain names and brand names are inextricably linked, but domain names that are confusingly similar to a brand name are all too easy to acquire — and exploit.
It’s not simply the top-level domain (the .com part of the domain) that poses a risk, either. More often than not, all it takes is incorporating a word/phrase like “customerservices” to a brand’s official domain name. Clients and prospects can be easily fooled into thinking it’s a legitimate domain, created to service a specific aspect of the business.
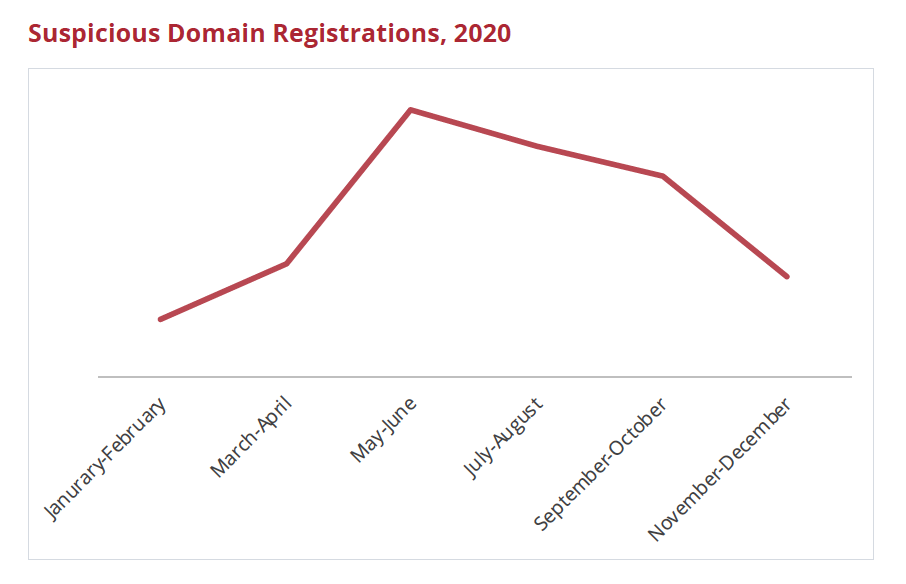
Another tactic is swapping out a letter in an official domain name for another letter or number. It’s easy to spot the difference between amazon.com and amaz0n.com in this sentence because of the context, but analyzing the sender’s domain name is not a natural act for everybody. Cybercriminals also took advantage of pandemic-distracted targets in 2020, with the number of suspicious domain registrations spiking 366% in May/June over January/February, according to the SOBP report.
Companies that fall victim to a spoofed domain scam stand a double loss. First, the lead that may well have gone on to become a sale is gone. Second, consumers may still hold the company responsible. According to the report, nearly half (48%) of consumers said they stopped using an online service when it suffered a data breach.
Actions to take: A company can’t possibly own every iteration of its legitimate domain name, but there are certainly a handful of near-miss “spoofed” domains — whether by innocent typo or easy letter substitution — that are inexpensive and logical to own. Make sure these “incorrect” URLs redirect to your official website. (Pro tip: By tracking the redirect, you can determine whether you might have a branding problem. For years, lego.com intercepted any traffic to legos.com with a note to visitors that its brand name was singular and not plural.)
As with email phishing, make sure employees have the training and tools to take suspicious domains seriously and have a process to report them.
Brand Page Impersonations Happen on Social Media
Another place where cybercriminals might be taking direct aim at your high-value prospect base is on social media. For example, it’s easy to create a fake company page on Facebook because the process requires nearly no authentication. With some lookalike graphics and the company’s official logo in hand, a bad actor can create an illegitimate Facebook page designed to target your market in half an hour.
With some promotion, posts (which might even be picked up from the legitimate page) and issuing an invitation, some of your legitimate audience can be easily fooled into participating with the new fake page. They might not even realize they’re engaging with an imposter, further impeding a company’s ability to turn social posts into customers.
Actions to take: Emphasize to your social media team or agency not to ignore imposter accounts, and put in place a process for what to do when they are found. Be sure these fake accounts are reported to the social network itself. All the major social media providers have mechanisms in place for reporting fraudulent pages.
The Brand Name Ad Blitz
While many disagree with Google’s policy that allows using company names as keyword ads, bidding on a company name is a standard way that cybercriminals can make off with your hard-earned leads. Google states that only a trademark owner can use a trademarked name in their ad copy,[3] but besides that it’s fair game.
It may not seem fair that you need to buy your own company name, but the expense may well be worth it. If your company doesn’t show up in the first few organic search spots, paying for your company name not only guarantees you a top result position, but it also helps block a bad actor from trying to make off with your good will.
Actions to take: Make the time to monitor the top search engines for your company name. If you find another organization appears ahead of you and is using your trademark in its ad copy, report it to Google, which will take down the competitor’s ad.
Reverse-Engineered Keyword Strategy
Of course, search engines are about much more than a company’s name. Just as competitors analyze each other’s web presences and search keyword strategies to reverse-engineer the best approaches for themselves, so can a cybercriminal make off with your high-ranking and high-performing SEO and SEM keywords by legitimately buying them. And when it comes to pay-per-click (PPC) ads, as long as a cybercriminal doesn’t use a trademarked word in their ad copy, a marketer can’t do much more than bid higher for the keyword than the criminal.
Actions to take: Consider engaging with a service that can assist with strategy and monitor your search ranking. If you lose a high-value keyword to a competitor or cybercriminal, compare its results page with yours, make some changes to try and regain your standing.
Verify Your Google My Business Account
Another way cybercriminals can make off with your leads is through a loophole in Google My Business Accounts. These accounts, designed to literally help put businesses on the map, need to be verified by the business or else any user can change critical details about the listing. Imagine seeing your company name but with a URL and phone number that doesn’t drive the lead to you.
Go to Google Maps and search for your company name. If the listing shows a “Suggest an Edit” button, that means anybody on the internet can make a series of potentially devastating changes, including changing the URL and phone number.
Action to take: In the Google Maps profile listing, look for a link that says either “Claim this Listing” (unverified) or “Manage the Listing” (verified). If your company name is not verified, make sure to verify it. Companies that are not listed in Google Maps at all need to go business.google.com and either start or verify the company listing.
The Bottom Line
Brand exploitation is more than a thorn in a marketer’s side. When a bad actor impersonates a brand, every click-through from a phishing email or a spoofed web page can steal a marketer’s lead — and potential sale. Organizations must proactively monitor for brand impersonation, which includes training staff, having a process in place for how to handle it and considering key technologies to stop cybercriminals before they can inflict any damage.
[1] “Projected 2021 Average Cost Per Lead by Industry and Channel,” Linchpin
[2] “Email Marketing ROI: What leads to better returns?,” Litmus
[3] “Trademarks,” Google
Subscribe to Cyber Resilience Insights for more articles like these
Get all the latest news and cybersecurity industry analysis delivered right to your inbox
Sign up successful
Thank you for signing up to receive updates from our blog
We will be in touch!

