A Mimecast plan that fits your organization’s needs
Mimecast offers multiple plans designed to meet your organization’s needs and enable you to Work Protected.
As the top attack vector, email demands the strongest possible protection. We block the most dangerous email-borne attacks, from phishing and ransomware to social engineering, payment fraud, and impersonation.

Email volume is increasing at 82% of organizations - higher than ever, leading to a greater volume of threats
59% of cybersecurity leaders believe growing attack sophistication is their biggest challenge
Key business decisions are being shaped around cyber risk due to the rise in awareness of email security risk
Apply the power of AI, machine learning, and social graphing to make security smarter and empower employees.
Choose your deployment option - email security delivered with or without a gateway.

Protect more than email by leveraging insights from across your security tools.
Improve protection with real-time threat analysis, using AI to remove threats before emails are opened.
Leverage industry-leading AI to defend against sophisticated business email compromise and impersonation attacks.
Block quishing attacks with QR code detection and deep URL scanning.
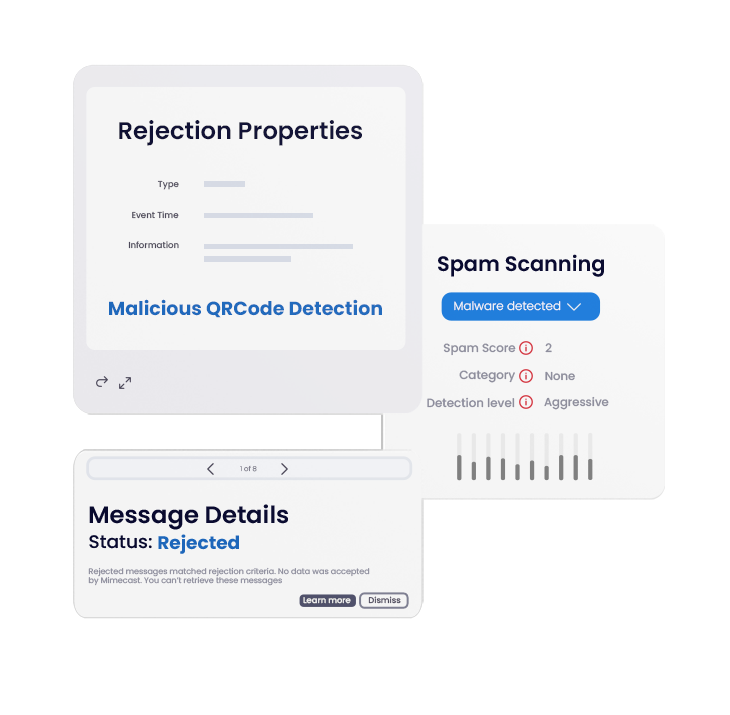
Protect against the most sophisticated malware threats with an AI-powered inspection service.
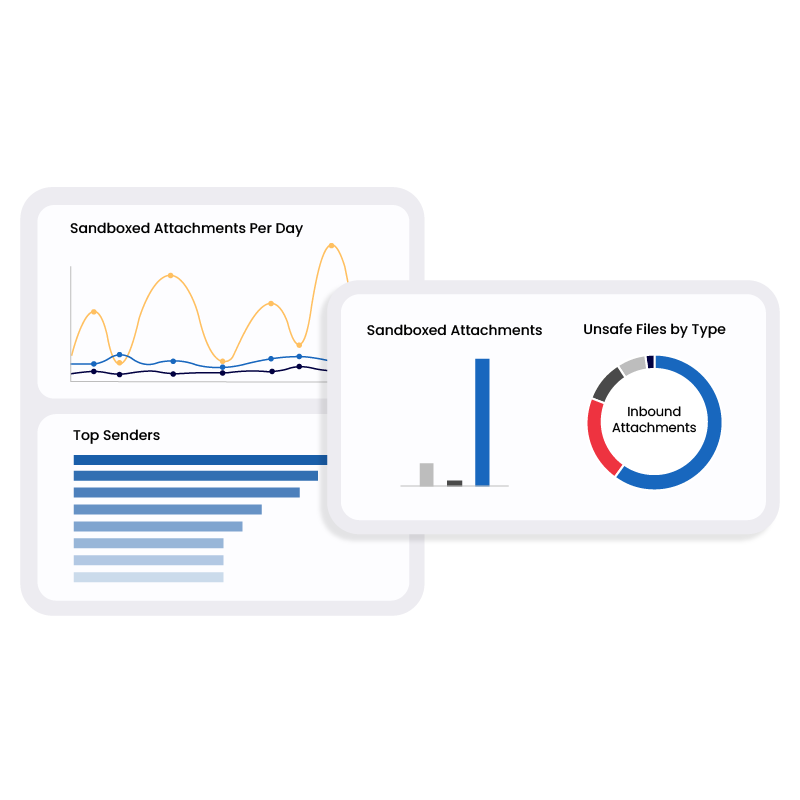
Enable threat sharing and enhanced detections with over 250 partner integrations.







Don’t take our word for it - Mimecast has protected organizations’ communications, people, and data since 2003.

Mimecast offers multiple plans designed to meet your organization’s needs and enable you to Work Protected.
Explore more details about email security.
Mimecast protects customers with multiple detection engines that pairs advanced AI and machine learning with industry-leading technologies tuned and improved over the past 20 years based on trillions of emails and millions of users.
Advanced email protection is a comprehensive, cloud-based enterprise-grade protection solution that guards email systems from a range of cyber attacks such as spam, viruses, and malware. As cyber threats constantly evolve, it's crucial for organizations of all sizes to implement advanced email protection.
Advanced email security products should provide organizations with:
Advanced email security products safeguard your business data by stopping the cyber attacks that lead to data exfiltration. Organizations should ensure their solutions offer the following features:
While every organization requires some form of advanced email security, the needs of each organization can vary based on their own specific environment. When choosing which advanced email security solution to choose, the following should be considered: