Threat Intelligence Briefing: Cybercriminals Weaponizing Keywords in Coronavirus Phishing Attacks
Coronavirus phishing attacks and domain registrations increase dramatically
This week’s Global Cyber Threat Intelligence Weekly briefing was the first in an ongoing series of interactive web sessions from Mimecast with the mission of helping customers and the general public better navigate their new normal – working from home to help stop the spread of the coronavirus (COVID-19).
The “new” normal also means new cyberattacks – or as was discussed on during Tuesday’s webcast – the same old attacks with new lures that capitalize on the understandable anxiety surrounding COVID-19.
“We’re seeing a weaponization of keywords,” said Mimecast Vice President of Threat Intelligence and IT-SAC Board Member, Josh Douglas. “When you think about it from an IOC perspective, we’re seeing a 28-times-increase since February 20th.”
Outside of China and its neighboring countries, Mimecast has observed a massive boom in blocked URLs in places like Iran, Italy, even Princess Cruises, Douglas said.
“They play on people’s anxiety,” Douglas said.
Mimecast’s panel of threat intelligence experts outlined best practices for remote workers, details on increases in COVID-19-related cyberattacks, and the rise in retail domain spoofing attacks.
5 Tips for Remote Workers
So much of the remote workforce today is new at this; social distancing has forced many people who have never worked from home to do so, and they’re relying on home infrastructure that’s beyond the scope of IT and IT security personnel’s immediate control, which reintroduces the challenge of shadow IT.
With that in mind, Mimecast offered the following 5 tips for remote workers:
- Update home WiFi with a strong password
- Update your personal contact information to assist in verification
- Never click on COVID-19 related attachments received outside your trusted perimeter
- Double-check URLs and links – if they’re suspicious, don’t click
- Update usernames and passwords on trusted sites only
We're seeing a huge surge in COVID-19-related phishing attacks, and noticing a significant increase in spoofed websites like news outlets, the CDC, WHO, etc. causing unsuspecting workers to click through and download viruses. This calls for an abundance of caution in everything we do, including checking the URLs independently before you click or download.
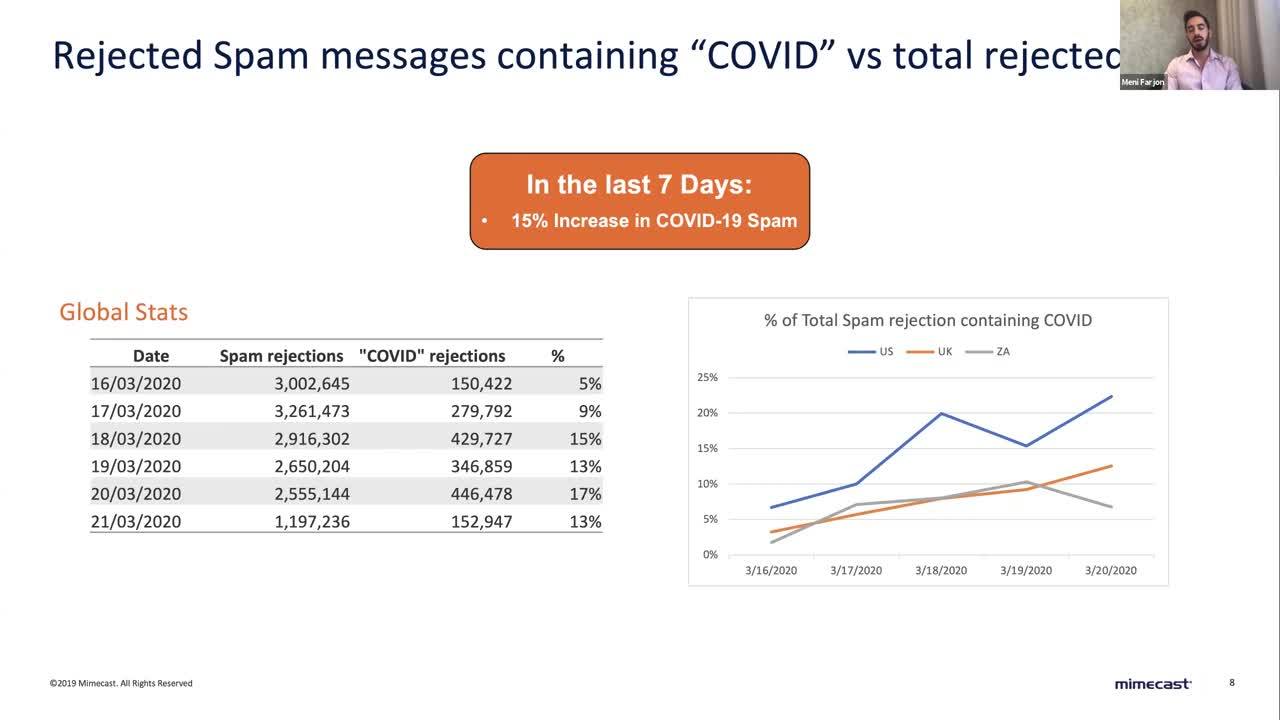
Increase in COVID-19 Campaigns
In the last seven days, Mimecast Threat Intelligence has seen a greater increase in spam; COVID-19-related spam email represents about 15 percent of overall volume.
“We’ve also seen an increase in the diversity of the methods in campaigns,” said Dr. Francis Gaffney, Director of Threat Intelligence at Mimecast. “For example, we saw emails targeting health professionals in the UK; it was regarding a staff seminar on the virus itself where targets are encouraged to enter their credentials in an application.”
Meni Farjon, Chief Scientist, Advanced Threat Detection at Mimecast, said he’s observed an increase in malware authors reusing previously popular exploits such as the Equation Editor exploit.
“What this teaches us is that attackers are somewhat relying on systems not being fully patched, especially if they’re not connected to the corporate network,” Farjon said. “Wherever you are, your systems must be patched.” He added that we’ve seen larger campaigns; instead of a thousand or two thousand targets, attackers seek to exploit hundreds of thousands of targets.
Malicious Actors Preying on Anxiety
Anxiety around the current state of affairs, has driven people to search online for information from local, state and federal sources. As a direct result of that, we’re seeing a weaponization of keywords.
Threat actors are using the headlines, preying on end users’ curiosities and anxieties.
“Companies throughout the entire world without protections on endpoints or on their home networks can be taken advantage of by threat actors to drive infection rates,” according to Douglas. “The key takeaway here is to think about the anxieties of employees and how we talk about things they may or may not be seeing. Security awareness and vigilance by employees is the last line of defense, so we need to make sure people understand what they’re seeing related to COVID-19 or even related to some incendiary language from leaders around the world.”
Rise in Retail Web Spoofing
As we’ve seen in a number of countries, there’s been a run on groceries and paper products at local stores or big box stores. If consumers can’t find things locally, they turn to the web for purchasing.
“We’ve tracked 60 thousand new domains in just the last two weeks, related to the words ‘COVID’ or ‘coronavirus’ – some are legit, but most are not,” according to Elad Schulman, VP of Brand Protection, Mimecast.
Schulman added to be aware of links; if you want to buy online, go to the site itself without following a URL that was emailed to you. Beware of these “too good to be true” promotions.
The Bottom Line
The attacks covered in this webinar related to coronavirus have not changed; attackers are using the same methods as they have in the past. That said, IT security professionals should monitor and patch consistently, particularly while remote work is underway. They can start with getting security into end users’ web browsers, products to protect web traffic, and constantly encourage best practices and promote robust security awareness training outlined here.
Unfortunately, shadow IT will likely be on the rise as employees look for workarounds to compensate for a slower, more cumbersome work experience. This will become much more of an issue than it was in the last three weeks, and is in line with the fact that organizations have had to accept more risk because of remote working.
Mimecast will continue to provide more information as it’s discovered. Sign up to put the weekly webcast on your calendar.
Watch the full webcast below!
Subscribe to Cyber Resilience Insights for more articles like these
Get all the latest news and cybersecurity industry analysis delivered right to your inbox
Sign up successful
Thank you for signing up to receive updates from our blog
We will be in touch!

