How Antispam Software and Ransomware Protection are Connected
Research from Mimecast Threat Center reveals a malware campaign delivered via sideloading, a new technique enabled by Windows 10, known to result in ransomware attacks.

Key Points
- A threat actor known for spreading malware such as Trickbot and BazarLoader has resurfaced, with a novel way of delivering malware, according to Mimecast’s Threat Center.
- The novel malware delivery method, known as “sideloading,” takes advantage of a feature Microsoft introduced in June 2021 allowing users to install Windows 10 apps from a webpage; sideloading seeks to install apps while bypassing the Windows store.
- Trickbot and BazarLoader deliver spam and are known to result in ransomware attacks, which demonstrates the importance of a secure email gateway and antispam software.
In June 2021, Microsoft released a new feature in the Windows store called the App Installer, which allowed users to install Windows 10 apps from a webpage. Unfortunately, a threat actor known for spreading Trickbot and BazarLoader, which deliver spam often resulting in ransomware attacks, has exploited this feature. This is yet another example of the importance of updated email antispam software to help prevent ransomware attacks.
Trickbot was first seen in 2016, and has largely been used to target financial firms; BazarLoader is essentially a spinoff of Trickbot to deliver malicious payloads via Microsoft and JavaScript attachments in spam emails that remain undetected until activated. Both aim to steal banking information, PII (personally identifying information), and/or user credentials.
The threat actor behind Trickbot and BazarLoader is known to sell access obtained from compromised networks to third parties that use it for ransomware. The use of sideloading to load the malicious payload is a new approach to an ever-evolving threat landscape.
How the Sideloading Threat Works
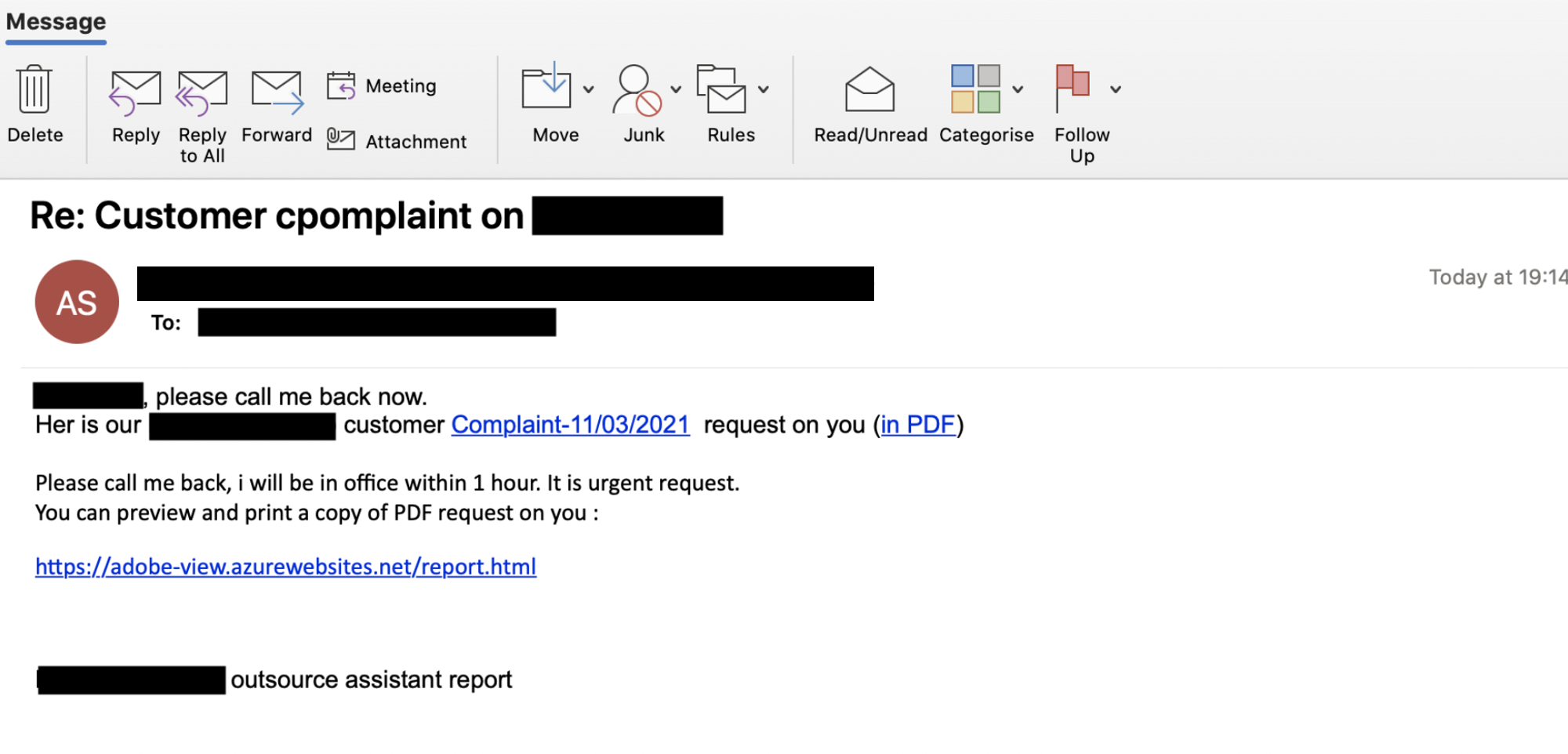
A spam email tricks users into clicking on what appears to be a legitimate link. The email concerns a customer complaint that references their full names, with further details available in the linked PDF. The intent, of course, is to create a sense of urgency to uncover the complaint. And the quickest way to find out is to click the link and download the report.
Note that the content of the email is grammatically awkward and contains a misspelling (“Her” instead of “Here”), a sure sign that this is possible spam. But if users are in a panic that a complaint supposedly is filed against them, they may not read the email carefully. (This is why effective antispam software is so critical – it would have caught the malicious content.)
The link looks legitimate. But instead of downloading the report, the malware uses sideloading to bypass the Windows App store webpage and install malware. The user clicks on the report thinking it is to download the PDF report. Instead, the link redirects to a webpage where it seems there is some problem and asks the user to try to download again.
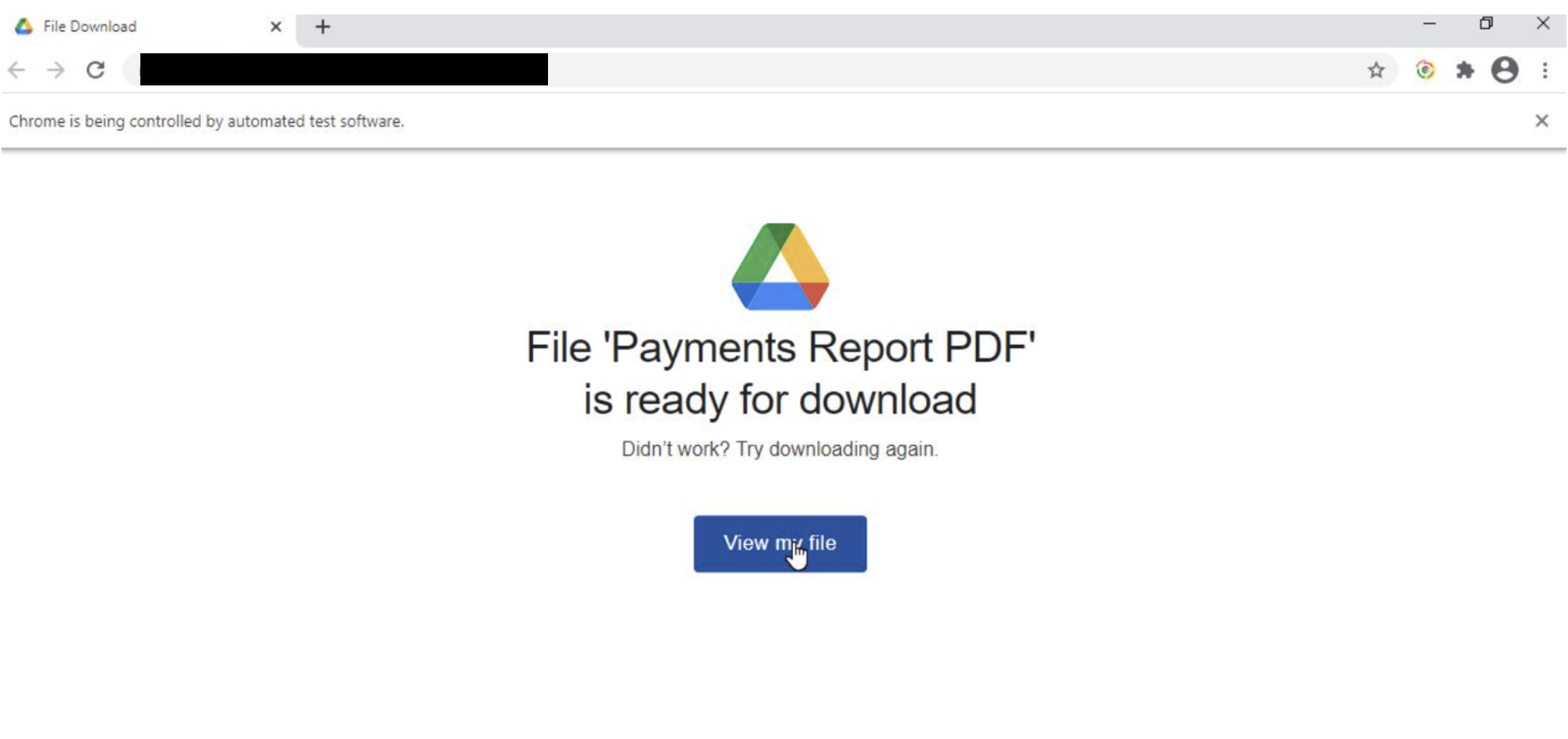
Sideloading Malicious Code
Instead of downloading the report, users are tricked into thinking they need an app to view the report. It looks above board, except it’s not.
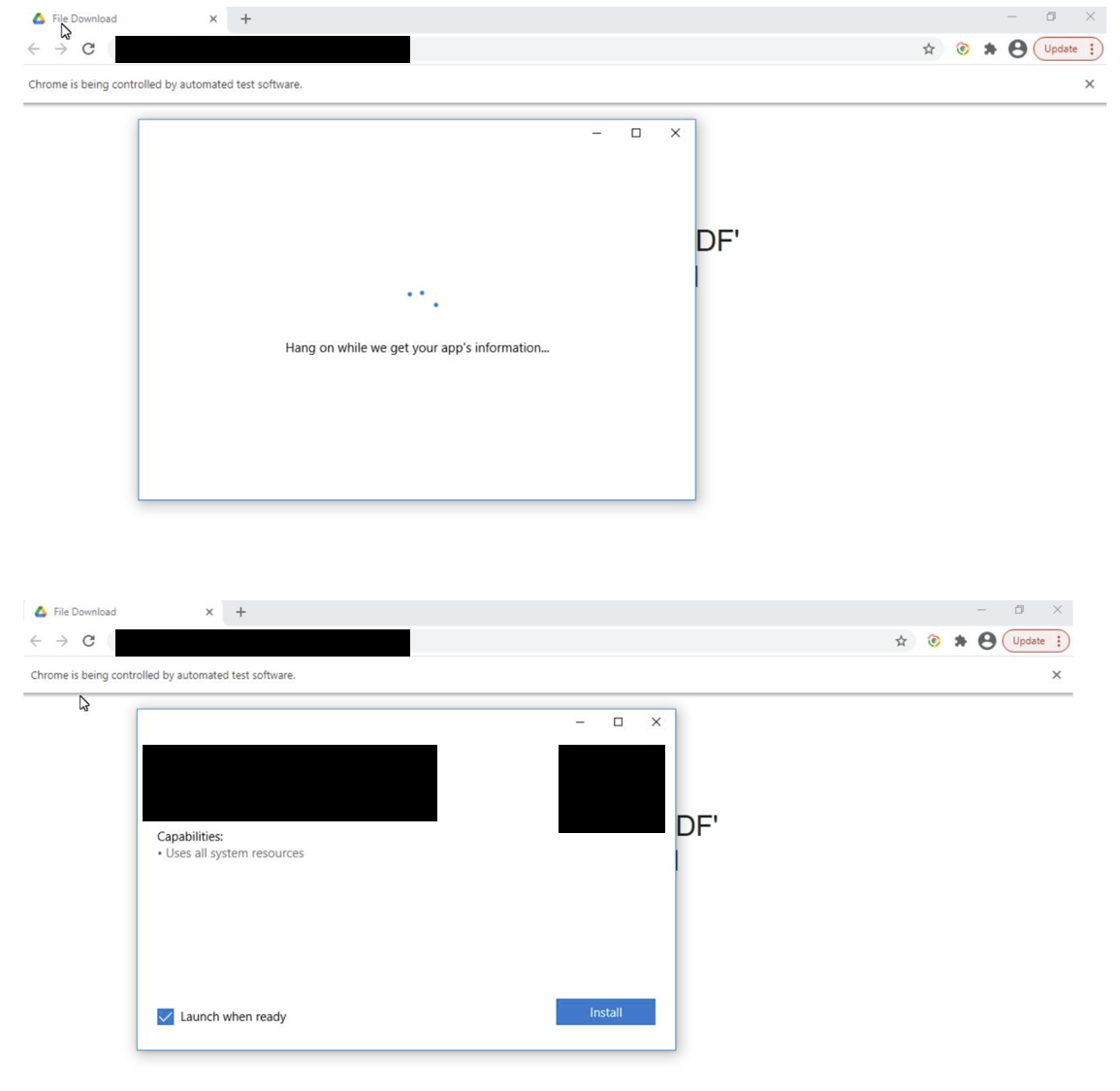
When users click Install, they download an app bundle used by Windows 10; the problem is that bundle contains the malware.
Mimecast Threat Center noted this campaign has been seen more than 16,000 times across varying countries, including the US, UK, Germany, Australia, and South Africa.
Defend Against Sideloading
Starting with Windows 10 2014, Microsoft turns on sideloading by default. Organizations can turn the feature off, though they then lose the ability to easily download apps not available in the Window app store designed for functions unique to their business.
Regardless of whether an organization chooses to allow sideloading, the first line of defense against ever-evolving threats such as this is a combination of effective antispam software and user awareness training. Multi-layered email security strategy delivers the efficacy required to keep your business, information, and users safe. Scanning emails and quarantining suspicious content helps prevent spam that leads to ransomware attacks.
In addition, user awareness training alerts employees to the key characteristics of spam to instill a “think before you click” mentality. In this example, a cyber-aware employee would be immediately suspicious of an email that contained misspellings and awkward grammar.
The Bottom Line
Cybercriminals continually seek new vulnerabilities to exploit users. This sideloading scheme is just the latest example. According to Mimecast’s Threat Center, this is a new twist on similar malware attempts masquerading as a Windows application - a particularly dangerous one that is sure to be imitated by other threat actors. The best defense is effective email antispam security updated with the latest threat intelligence combined with a culture of “think before you click” through continual user awareness training.
Subscribe to Cyber Resilience Insights for more articles like these
Get all the latest news and cybersecurity industry analysis delivered right to your inbox
Sign up successful
Thank you for signing up to receive updates from our blog
We will be in touch!

