Frequently Asked Questions
Explore more details about Collaboration Security.
What is collaboration security?
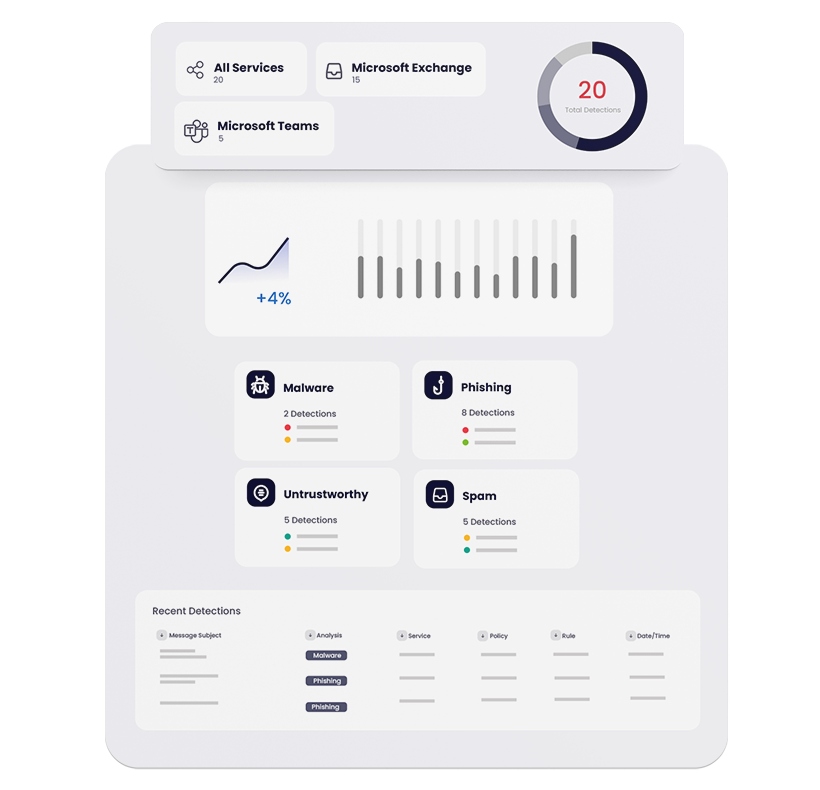
Collaboration Security is technology that is used to keep dangerous content – like malware, phishing, and viruses – out of tools that employees use for instant messaging, file sharing, etc. Some examples of collaboration tools include Microsoft Teams, Microsoft OneDrive, Microsoft SharePoint, and Slack.
Why is collaboration security important?
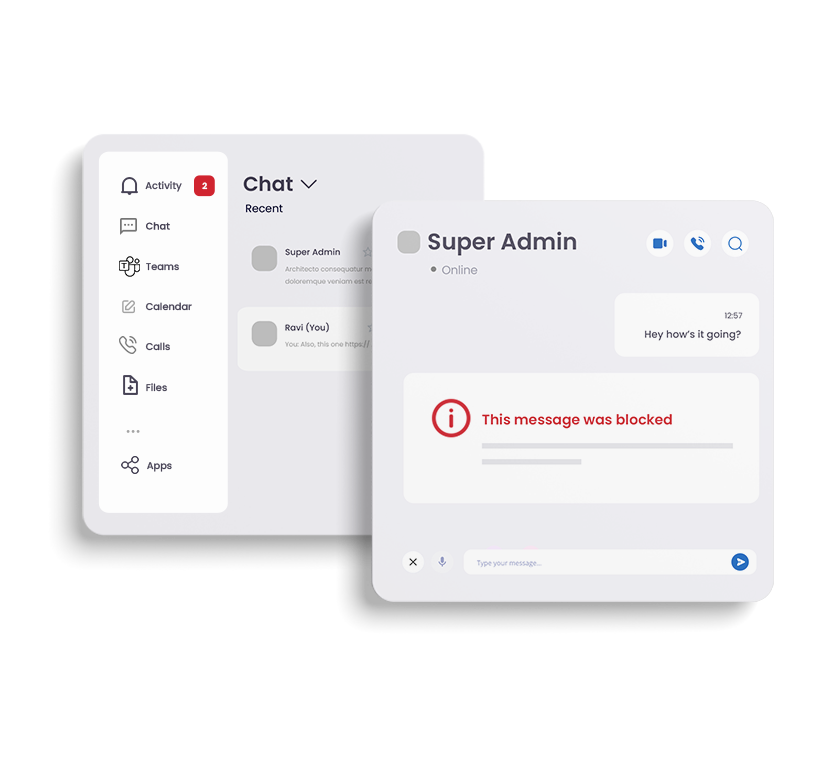
Collaboration tools like Microsoft Teams may seem quite different to email, but the risks they pose are the same and possibly even greater. Guest access is usually enabled by default, giving third parties easy access to your environment. The instantaneous nature of these platforms means that dangerous content can spread like wildfire, and employee trust in these tools borders on absolute. Without protections in place, organizations leave the door open to dangerous and costly cyberattacks.
Why is Microsoft Teams Protection important?
Adoption of M365 has skyrocketed, which makes Microsoft an extremely valuable target for cyber criminals. Attacks against this platform are relentless. Following the best practice of layered security and having the strongest possible protections in place is essential.