What is an Impersonation Attack?
An impersonation attack is a form of fraud in which attackers pose as a known or trusted person to dupe an employee into transferring money to a fraudulent account, sharing sensitive information (such as intellectual property, financial data or payroll information), or revealing login credentials that attackers can used to hack into a company’s computer network. CEO fraud, business email compromise and whaling are specific forms of impersonation attacks where malicious individuals pose as high-level executives within a company.
Stopping an impersonation attack requires strong security policies and vigilance on the part of employees. But because these attacks are designed to take advantage of human error, you also need solutions that can automatically scan email and block any potential attack. That's where Mimecast can help.
What is an Email Impersonation Attack?
Email impersonation attacks are a type of phishing attack where the attacker impersonates a legitimate sender in order to trick the recipient into clicking on a malicious link or attachment.
These attacks are typically used to steal sensitive information such as login credentials or financial information. In some cases, attackers may also use email impersonation to deliver malware to the victim's system.
Email impersonation attacks can be difficult to detect, as the attacker will often use a fake email address that is similar to the legitimate sender's address. If you receive an email from an unknown sender, or if the email contains grammar or spelling errors, these may be signs that it is an impersonation attack.
If you are unsure whether an email is legitimate, you can always contact the supposed sender directly to verify its authenticity. Remember, never click on any links or attachments in an email unless you are certain that they are safe.
How does an Impersonation Attack Work?
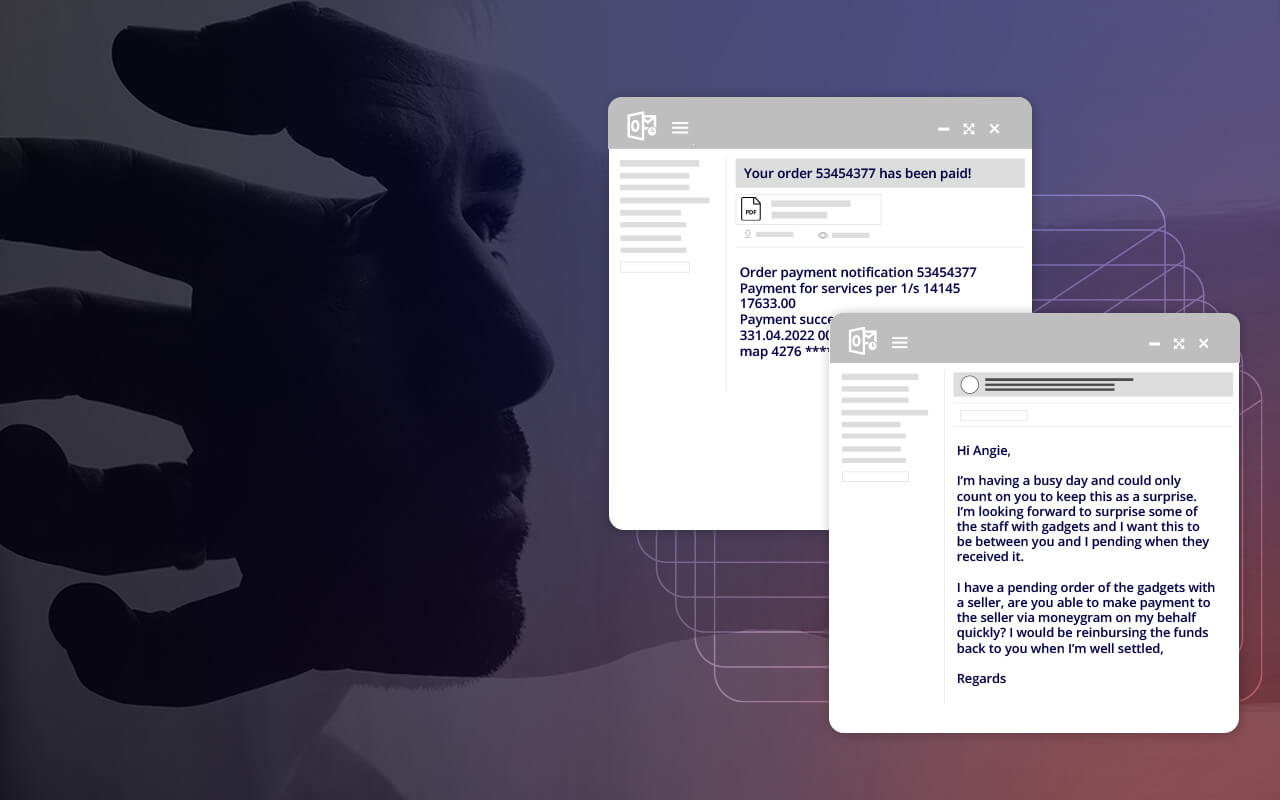
Impersonation attacks are typically malware-less attacks conducted through email using social engineering to gain the trust of a targeted employee. Attackers may research a victim online, gathering information from social media accounts and other online sources which, when used in the text of an email, can lend authenticity to the message. An impersonation attack is typically directed at an employee who can initiate wire transfers or who has access to sensitive or proprietary data. The employee receives an email that appears to be from a legitimate source, often a high-level executive within the company, urgently requesting that money be wired to a certain account or that sensitive information be sent immediately.
What Are Common Email Impersonation Attacks?
- Urgent, short-notice requests that involve the transfer of money or sensitive information such as bank account information or login credentials.
- Purchase requests to be completed on behalf of the CEO, often gift cards.
- Employees abruptly requesting changes to direct deposit information.
- Creating emails with slight name deviations such as writing the letter "m" as "rn".
- Using language that induces urgency and a sense of fear.
How to Recognize an Impersonation Attack?
Unlike common phishing attacks, which are often unspecific and filled with grammar or spelling mistakes, impersonation attacks are highly targeted and well-crafted to appear realistic and authentic. There are a few things, however, that point to a potentially fraudulent email:
- An urgent and possibly threatening tone. Most impersonation attacks request or demand that the recipient act immediately. Some impersonation emails may threaten negative consequences if the recipient doesn't act quickly enough. This is intended to prevent the employee from taking time to double check before acting.
- An emphasis on confidentiality. Some impersonation attacks will suggest that the action is part of a confidential development or secret program that should not be discussed with colleagues or immediate superiors.
- A request to send money or share sensitive information. Any request to transfer money or to release sensitive financial data, payroll information or intellectual property should be corroborated through multiple channels.
- A problem with email addresses or links. Often, the email impersonating an executive will be a slightly altered version of a legitimate email address. Additionally, the reply-to address may be different than the sender's address, or the actual links to URLs within the email don't match the text in the hyperlinks in the body of the email copy.
- Unusual requests or accounts. Impersonation attacks frequently request recipients to send money to bank accounts or vendor accounts that have different numbers than the employee has used in the past.
How to Avoid an Impersonation Attack?
Scams involving an impersonation attack pose a significant danger to companies of every size. Rather than using malicious URLs or attachments, an impersonation attack uses social engineering and personalization to trick an employee into unwittingly transferring money to a fraudulent account or sharing sensitive data with cyber criminals.
An impersonation attack typically involves an email that seems to come from a trusted source. Sometimes the email attack may start with a message that looks like it comes from a CEO, CFO or another high-level executive – these scams are also called whaling email attacks. An impersonation attack may also involve a message that appears to be from a trusted colleague, a third-party vendor or other well-known Internet brands. The message may request that the recipient initiate a transfer to a bank account or vendor that later proves to be fraudulent, or it may ask the recipient to send along information like W-2 files, bank information or login credentials that give hackers access to business finances and systems.
Stopping an impersonation attack requires strong security policies and vigilance on the part of employees. But because these attacks are designed to take advantage of human error, you also need solutions that can automatically scan email and block any potential attack. That's where Mimecast can help.
Combating an Impersonation Attack with Mimecast
Mimecast makes email safer for business by combining solutions for email security, email continuity and email data protection into a single cloud-based service. By streamlining administration and providing a single cloud platform that covers all email functions, Mimecast reduces the cost and complexity of business email management.
Mimecast's SaaS email security services include protection against all major threats. In addition to stopping an impersonation attack, Mimecast can help prevent a ransomware attack, spear-phishing attack and insider attack as well as threats from viruses and malware. In addition to threat response solutions, Mimecast security offerings also include solutions for sending messages and large files securely, and for content control and data loss prevention.
Mimecast Technology for Addressing an Impersonation Attack
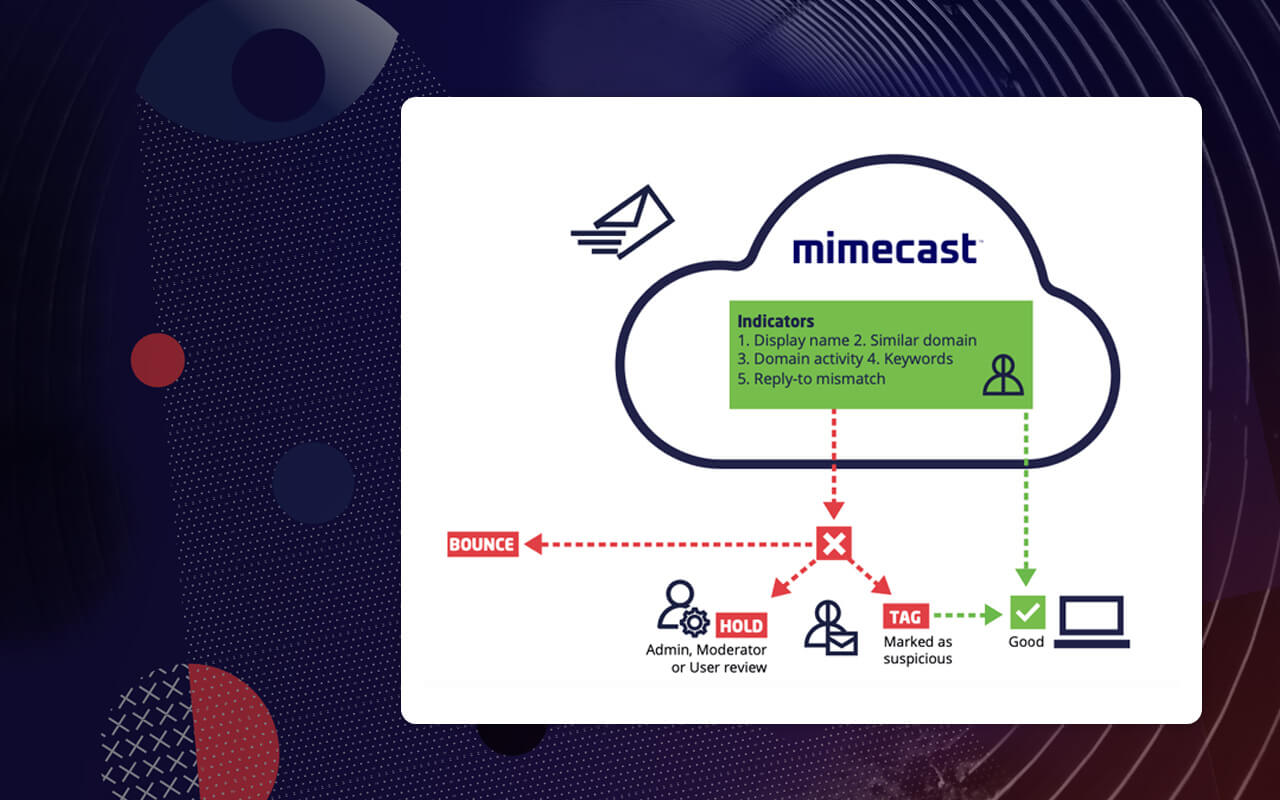
Mimecast scans all inbound, outbound and internal email to provide URL protection against malicious links, as well as attachment protection that scours attached documents for potential malware. But because many impersonation attacks are malware-less, Mimecast technology also searches the email and its content for signs of an impersonation attack. These include anomalies in:
- Display name
- Domain name
- Reply-to information
- Body of the message
If an email fails a certain combination of these tests, Mimecast can be configured to discard the message, quarantine it or send it on to the recipient with a warning that the message may be an impersonation attack.
Learn more about stopping an impersonation attack with Mimecast.
Impersonation attack FAQs
Who Are at a Risk of an Impersonation Attack?
While anyone could be at risk for an email impersonation attack, new employees are often prime targets. New employees are less likely to be familiar with the company culture and how members of the organization communicate or delegate tasks, so in their eagerness to create a good impression they may fall victim to an impersonation attack.
Why Are Impersonation Attacks Hard to Detect?
Impersonation attacks are carefully crafted and unique to each organization they target. Whereas generic "mass-market" ransomware emails often have obvious spelling and grammar errors, impersonation attacks are designed to look and sound like they came from prominent members of an organization. To the untrained and unsuspecting eye, it can be difficult to catch signs of an impersonation email, or even know where to look for them.
How to Stop an Impersonation Attack?
To prevent impersonation attacks and other forms of phishing and cybercrime, organizations are wise to adopt a multi-layered approach to email security that includes:
- Security awareness training that educates employees about what impersonation attacks look like, what can be done to prevent them, and the kind of damage that a successful attack can cause.
- Anti-impersonation solutions that scan email for signs of malware-less, social engineering-based attacks that are most commonly associated with impersonation. These may include header anomalies, domain similarity, sender spoofing and suspect language in the content of emails.
- Email security software that scans and filters every link and attachment in every email, blocking users from visiting URLs or opening attachments that may be malicious.
- DNS authentication services that use DKIM, SPF and DMARC protocols to identify legitimate and potentially fraudulent email.
- Anti-malware and anti-spam protection that can stop certain attacks from reaching user mailboxes.
How to report an impersonation attack?
When employees suspect they have been targeted or have been involved in an impersonation attack, they should immediately report the incident to their supervisor, to the IT department and to the person within the organization who was impersonated. Additionally, impersonation attacks can be reported to government organizations dedicated to preventing cybercrime. These include the Federal Trade Commission (www.ftc.gov/complaint), the Cybersecurity and Infrastructure Security Agency (phishing-report@us-cert.gov) and the Anti-Phishing Working Group (https://apwg.org/reportphishing/).