Email Attacks in the Real World: Examples For Your Resilience Strategy
Take lessons from the past in building your organization's cyber resilience strategy.
The 2019 State of Email Security report highlights some of the most alarming trends in the world of email security, but also examines how organizations are using advanced protection, awareness training and threat intelligence to combat these trends.
When it comes to understanding your ability to put together a plan for cyber resilience, it’s helpful to see how these attackers may go after your prized assets.
The Mimecast Threat Center team has found several point-in-time instances of the attacks and response techniques we explored in this year’s State of Email Security report. In this blog, we’ll detail the attacks adversaries may use to attempt to compromise your organization. These examples provide lessons you can use as you build your cyber resilience strategy.
Impersonation and Phishing Attacks: Rising and Worsening
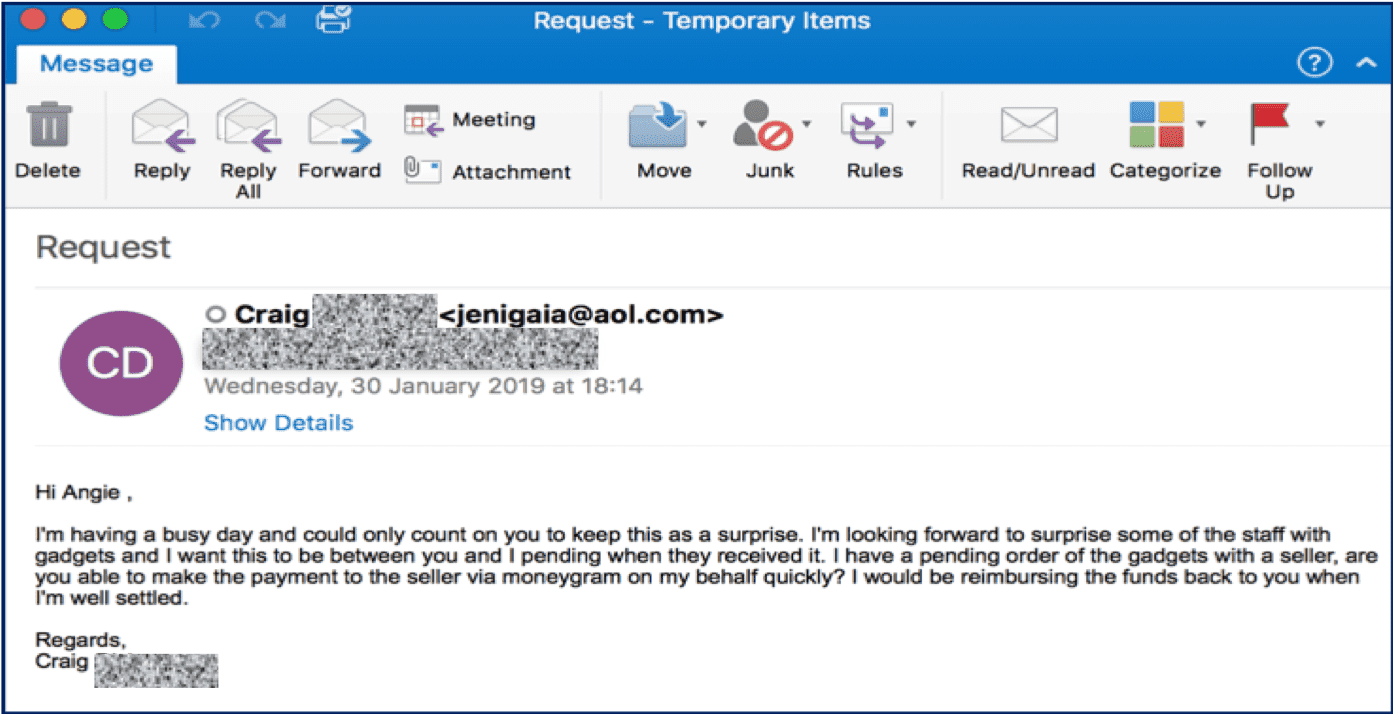
On Jan. 19, 2019, a CEO impersonation attack targeted a user at a Mimecast Legal customer—specifically targeting an individual involved with financial matters.
This was not an aggressive email that placed a lot of pressure on the individual as we often see. This one took a different social engineering approach to manipulate the victim.
The attacker impersonated the CEO and claimed to be too busy to conduct a payment himself and states there is an order of “gadgets,” indicating that the price to be paid is not likely to be small.
Furthermore, the attacker states they would like the activity to be kept quiet and between themselves and the victim. From a social engineering perspective, this email is not intimidating and appeals to the victim as a heartfelt gesture from the CEO to the team and therefore victims are more likely to obliged to follow through with the transaction and keep it quiet as instructed rather than flagging the transaction as suspicious.
Falling for this action can have serious consequences beyond just loss of company funds. One employee was sued after falling for a CEO fraud scam.
Awareness Training
The following malicious link was clicked on and blocked by Targeted Threat Protection – URL Protect 22 times by 22 unique users, mostly from government organizations. Users included directors and senior IT managers. Interestingly, all of the users who had clicked on this link had also clicked on other links leading to malware. One user (an infrastructure administrator) clicked 157 malware links during the last month.
hxxp://45.55.211.79/[.]cache/untitled[.]exe
The link downloads the new Sodinokibi ransomware. This ransomware encrypts and renames files with a random ID that is unique to each victim. A ransom note is left for the victim, with instructions on how to recover their files.
When the victim follows these instructions they are told how much they have to pay and by when, based on their unique ID. There are step-by-step instructions and even a chat support window should the victim need to further help, or want to attempt to negotiate the price (which was not successful in this case).
Internal Threats and Data Leaks
One customer was using a legacy domain which they had not protected with Mimecast. We observed a user opening an attachment – a Microsoft Word document. This attachment was actually a malware dropper and upon opening, the user became infected with the Trickbot banking trojan. One minute later, the Trickbot malspam module had emailed that attachment to hundreds of internal and external contacts from the compromised user’s account. We then saw further evidence of users from the legacy domain opening these attachments.
Trickbot can also use the EternalBlue vulnerability, made famous by WannaCry, to spread through a company’s network, infected machines on the network will re-infect machines that have been cleaned. Traditionally Trickbot has been used to steal financial information, such as credentials for online banking services. However, it is now also being used as a dropper for other malware including Ryuk ransomware, which is used against enterprise environments in highly targeted attacks with the ransom tailored depending on the size and value of the victim company.
Subscribe to Cyber Resilience Insights for more articles like these
Get all the latest news and cybersecurity industry analysis delivered right to your inbox
Sign up successful
Thank you for signing up to receive updates from our blog
We will be in touch!

