GandCrab Ransomware Attacks Exploit Valentine’s Day Weaknesses
This Valentine’s Day, your big heart could get you in trouble.
When you think Valentine’s Day, candy hearts, roses and chocolate are probably the first things that come to mind. Perhaps the last thing would be insidious email attacks, but this year a group of cybercriminals have brought that idea to the forefront.
In the run-up to this year’s Valentine’s Day, cybercriminals played on people’s emotions to entice them to click on malicious URLs and open malicious attachments, according to new research from the Mimecast Threat Labs team.
The threat actors behind GandCrab, or cybercriminals using GandCrab as a Ransomware-as-a-Service (RaaS), have used this Valentine’s Day to target victims. While GandCrab has only been around for about 12 months, it’s been a hugely successful RaaS campaign.
Features of the campaign include the ability to detect Russian victims (and stop the infection if they have a Russian-configured keyboard) and individual ransom notes. This signals these campaigns are specifically designed to not target Russian users.
Get articles like this delivered to your inbox every week. Subscribe to Cyber Resilience Insights today.
Threat Labs researched cyberattacks and email campaigns during holiday seasons and events over the last six months to understand how these events can be manipulated to target businesses. Campaigns around the holiday season often target personal email accounts, however, threat actors are increasingly targeting business emails with the same vigor and taking advantage of individuals looking to get special deals on presents for loved ones. This can be especially impactful for smaller IT organizations that may not have strong backup processes or the right security posture.
These holiday events also offer the opportunity for threat actors to harvest a vast amount of information and data that is input into online shopping websites by coming up with fake websites and fake customer surveys that promise to deliver anything from fake vouchers to ‘great deals’ to the victim.
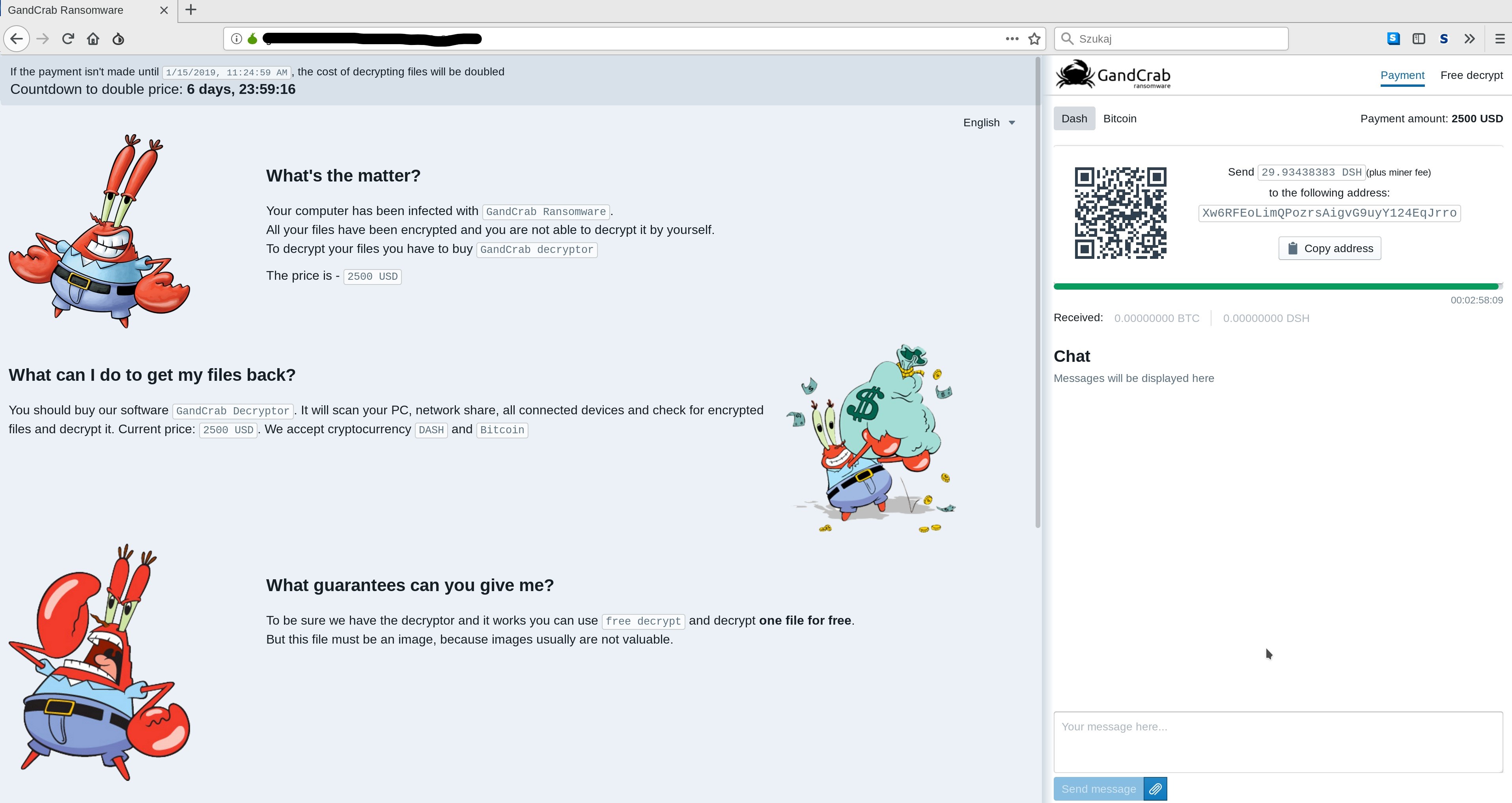
What is GandCrab ransomware?
GandCrab is unique for ransomware in that upon compromise it encrypts the files of the victim, and changes the file extensions, which are randomly generated. The text file with the ransom note also appears at the top of the victim’s desktop. When opened, the text files show how the victim’s files have been changed to a randomly-generated file extension. Each text file also contains a URL with a unique token, highly likely used to identify the victim. There can be large monetary differences in the ransoms between two different victims based on the value of the data.
Paying the ransom is made as easy as possible for the victims, as the URL from the text file walks them through paying with cryptocurrency in a simple manner. This leads to increased profits from vulnerable victims and those who are willing to pay the price of getting their files back in the quickest and easiest manner possible.
Additionally, the research confirms the threat actors are demanding Bitcoin or DASH as payment to release the GandCrab decryptor tool to victims.
How was Valentine’s Day exploited by threat actors?
Some of the key areas where threat actors target victims around Valentine’s Day included:
- Fraudulent emails offering gifts, flowers and other services, often the gateway to victims downloading malicious attachments, clicking on URLs that take them to phishing sites or clicking on malicious URLs that can download malware and ransomware. Some of the services around this date include special offers on Valentine’s Day dinners.
- Fake E-greetings, entices the victim to click on the email and open malicious attachments or click on malicious URLs within the body of the email.
- Fake online customers surveys, used to harvest personally identifiable information (PII) credentials around Valentine’s Day.
- Fake advertisements and websites, used to harvest financial credentials around Valentine’s Day.
- Malicious dating apps, used to harvest PII and financial credentials around Valentine’s Day.
- Hacked dating apps and websites, used to harvest PII and financial credentials held within their databases around Valentine’s Day.
We will note that GandCrab has been putting love-themed messages into their attacks for some time in advance of Valentine’s Day, as discovered by the Mimecast Threat Labs team.
When these tactics are successful, threat actors can use the PII exposed in other campaigns, sell it to other threat actors, use it in identity theft or, possibly, blackmail and extort if the attack has been targeted against a specific individual or entity.
What happens next with GandCrab?
It is likely the threat actor group behind GandCrab will continue to update the code over the coming 12 months, adding new features and ironing out any issues, along with offering GandCrab as a RaaS to increase their profits.
To prevent this kind of attack from harming your users and your business at large, implementing the strongest protection against malicious emails, attachments, links and websites is critical. We also recommend strong backup and recovery capability to minimize downtime. Without it, your business could face loss of money after paying ransom and loss of productivity in recovering from the attack.
Learn more about how to safeguard against ransomware attacks here.
Subscribe to Cyber Resilience Insights for more articles like these
Get all the latest news and cybersecurity industry analysis delivered right to your inbox
Sign up successful
Thank you for signing up to receive updates from our blog
We will be in touch!

