What is a whaling phishing attack?
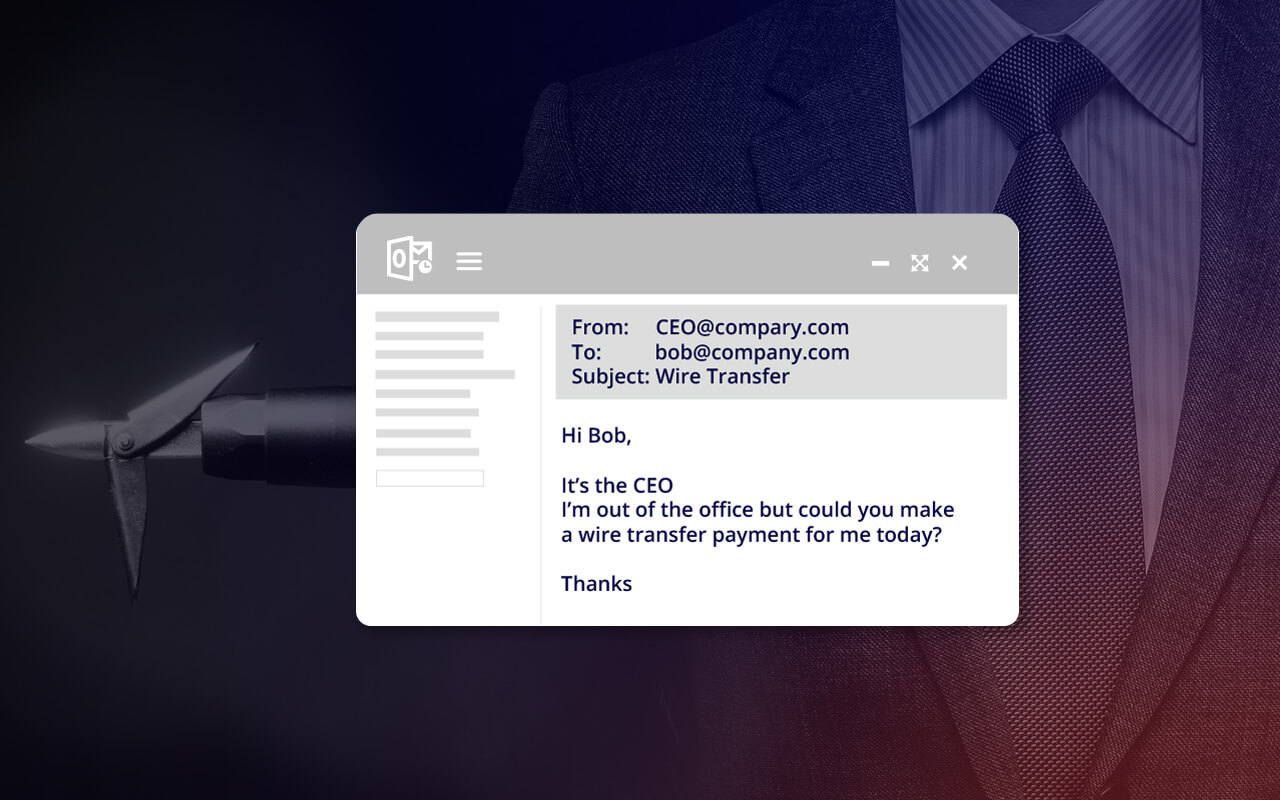
A whaling attack is a type of spear-phishing attack directed at high-level executives where attackers masquerade as legitimate, known and trusted entities and encourage a victim to share highly sensitive information or to send a wire transfer to a fraudulent account.
How does a whaling phishing attack work?
In a whaling attack, attackers send an email that looks and seems like a legitimate email from a trusted source, often a contact within the company or with a partner, vendor, or customer account. A whaling email will contain enough personal details or references gleaned from internet research to convince the recipient that it is legitimate. Whaling attacks may also ask a user to click on a link that leads to a spoofed website that looks identical to a legitimate site, where information can be collected, or malware can be downloaded. In a whaling attack, victims may be encouraged to share sensitive data like payroll information, tax returns or bank account numbers, or they may be asked to authorize a wire transfer to a bank account that turns out to be fraudulent. For attackers, the goal of a whaling attack is usually to steal money or data, or to get access to networks that can yield much larger ill-gotten gains.
Are your executives vulnerable to a whaling attack?
A whaling attack is a kind of phishing scam and CEO fraud that targets high profile executives with access to highly valuable information. In a whaling attack, hackers use social engineering to trick users into divulging bank account data, employee personnel details, customer information or credit card numbers, or even to make wire transfers to someone they believe is the CEO or CFO of the company. Whale phishing is generally more difficult to detect than standard phishing attacks, as these attacks often do not use malicious URLs or weaponized attachments.
Whaling attack instances are on the rise in the U.S., up more than 270% from January to August 2015. The FBI reports that business losses due to a whaling attack totaled more than $1.2 billion in just over two years1.
To improve whaling security, organizations need advanced threat protection that specifically defends against a whaling attack.
Whaling phishing examples
- Intercepting and interrupting an unencrypted email conversation to divert a large bank transfer.
- Setting up a fictional meeting with a malware link disguised as a zoom link.
- Requesting payroll information about current and past employees.
How to recognize a whaling attack
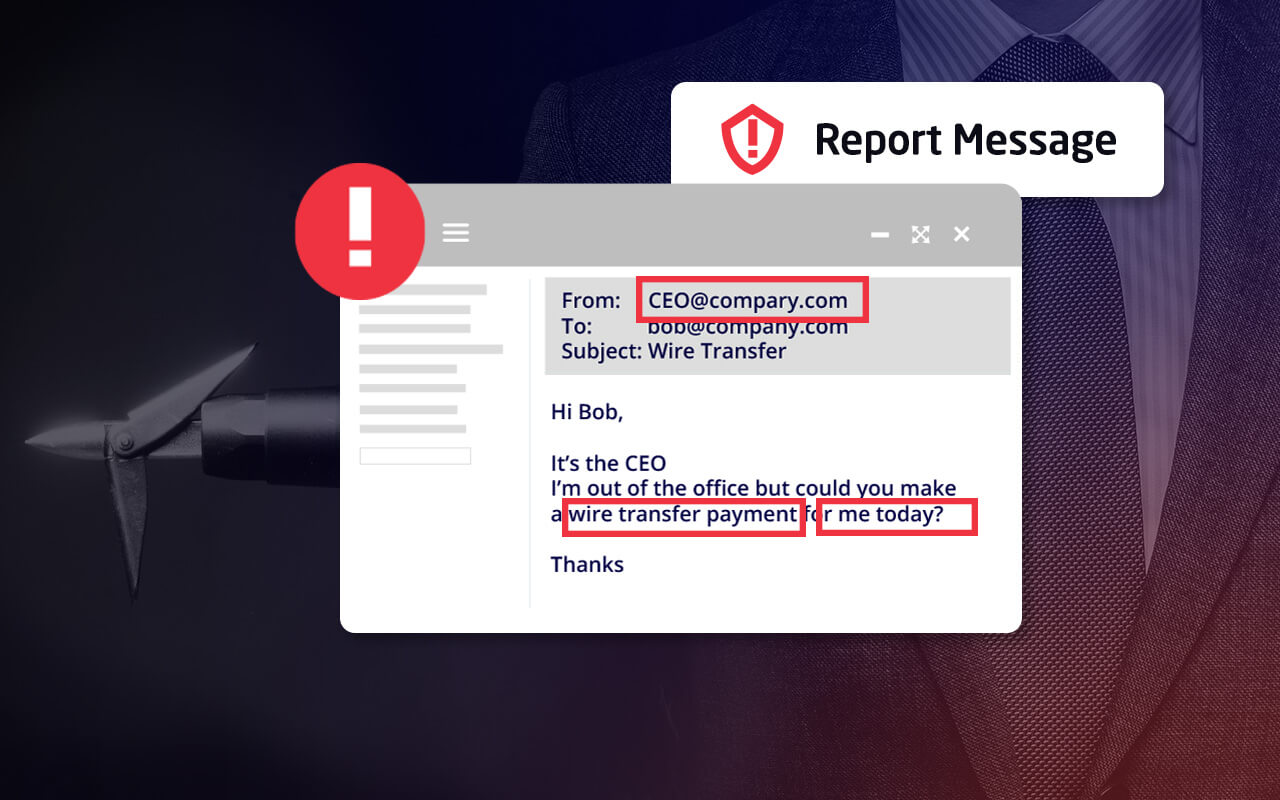
A whaling attack is much harder to recognize than a standard phishing attack, as attackers will usually invest much more time to make email communications and websites look legitimate. Some common signs that an email may be part of a whaling attack include:
- A sender’s email address that is not an exact match of the domain of the company the email claims to be from. For example, attackers will often substitute an “m” in a domain name with an “r” and an “n”, or “rn”, to fool the recipient.
- A request to share sensitive information or to wire money to an account.
- A sense of urgency that encourages the recipient to act quickly, with a hint or a threat of adverse consequences if the requested action isn’t performed right away.
How to block a whaling attack
Stopping a whaling attack requires a multi-layered approach to security.
- Strong anti-spam and anti-malware programs may stop some whaling attack emails at the email gateway.
- DNS authentication services that use DMARC, DKIM and SPF protocols can identify whether an email sent from a specific domain is legitimate or fraudulent.
- Email scanning and filtering technology can scan links and attachments within email in real time to determine whether they are suspicious, and to prevent users from accessing them.
- Anti-impersonation software can block a whaling attack by identifying the social-engineering-based techniques that are common to whaling emails.
- Security awareness training can help users to spot whaling attacks, and to adhere to protocols (such as confirming a wire transfer by a second means of communication) that can mitigate the damage of an attack.
Prevent whaling phishing with Mimecast
As a leading provider of cloud-based email services for security, archiving, and continuity, Mimecast offers Targeted Threat Protection with Impersonation Protect to safeguard organizations and their employees and financial assets from a whaling attack.
Impersonation Protect offers instant and complete protection from this advanced form of cyberattack, scanning and evaluating all incoming email for potential attack indicators. Mimecast examines:
- The sending domain name to identify whether the sender’s domain is a near match to the recipient’s domain name. A whaling attack will often use a domain name that looks very much like a trusted domain name, but with subtle and almost imperceptible changes.
- The display name or friendly name, to determine whether the sender is attempting to spoof an internet email address.
- The age of the sending domain — a newly registered domain name is more likely to be suspicious.
- Keywords in the body of the message, including phrases such as a “bank transfer” or “wire transfer”, which are often suspicious.
When Impersonation Protect identifies a suspicious email, it may be bounced, quarantined, or tagged as suspicious, with warning notifications sent to the intended recipient.
Key features of Mimecast’s solution for stopping a whaling attack
Mimecast provides whaling and spear security with features that include:
- Defense against social-engineering attacks.
- Administrative control over security procedures for suspicious emails.
- Comprehensive protection provided by Mimecast’s threat intelligence infrastructure and Messaging Security teams.
Learn more about thwarting a whaling attack with Mimecast and about Mimecast solutions for secure file transfer and spam email protection.
Whaling phishing FAQs
What type of phishing attack is whaling?
Simply put, a whaling attack is a phishing attack that targets and/or impersonates C-suite-level members of an organization. Posing as leaders within an organization often lures colleagues and/or employees into leaking data or credentials that help cybercriminals infiltrate the targeted organization.
What to do in a whaling phishing attack
If you suspect you have received a whale phishing email or are under attack, there are several immediate steps you can take to mitigate the damage.
- Disconnect your computer from the network and/or the internet in order to stop any malware from downloading or spreading.
- Alert your company immediately, giving your IT department a head start on limiting the damage and warning other employees about potential attacks.
- Scan your computer for viruses and malware that may have been downloaded as part of the attack.
- Change your login credentials and passwords immediately to prevent attackers from using any information you have shared to access your accounts.
Report the whale phishing attack to the Federal Trade Commission (ftc.gov/complaint), the Cybersecurity and Infrastructure Security Agency (phishing-report@us-cert.gov), and the Anti-Phishing Working Group (apwg.org/reportphishing).
How to report a whaling attack
An attempted or successful whaling attack should be reported immediately to a variety of people. Victims should immediately alert their employer and its IT department in order to take quick action to block other attempts or to stop attackers from doing further damage. Whaling attacks can be reported to a number of organizations dedicated to helping to prevent cybercrime such as the Federal Trade Commission (www.ftc.gov/complaint), the Cybersecurity and Infrastructure Security Agency (phishing-report@us-cert.gov), and the Anti-Phishing Working Group (apwg.org/reportphishing).