Splunk
Developed by Mimecast
Identify Threats & Inform Response
Email continues to be the most widely used attack vector. Data sourced from email activity and attacks is high value for the security operations team, enhancing the benefits of your Splunk Enterprise investment.
Splunk can ingest Mimecast logs, along with other log sources, to obtain complete visibility across all environments. Correlate security events detected by Mimecast Targeted Threat Protection and the Secure Email Gateway with other security systems connected to Splunk Enterprise – helping security analysts detect incidents and attacks quickly and accurately.
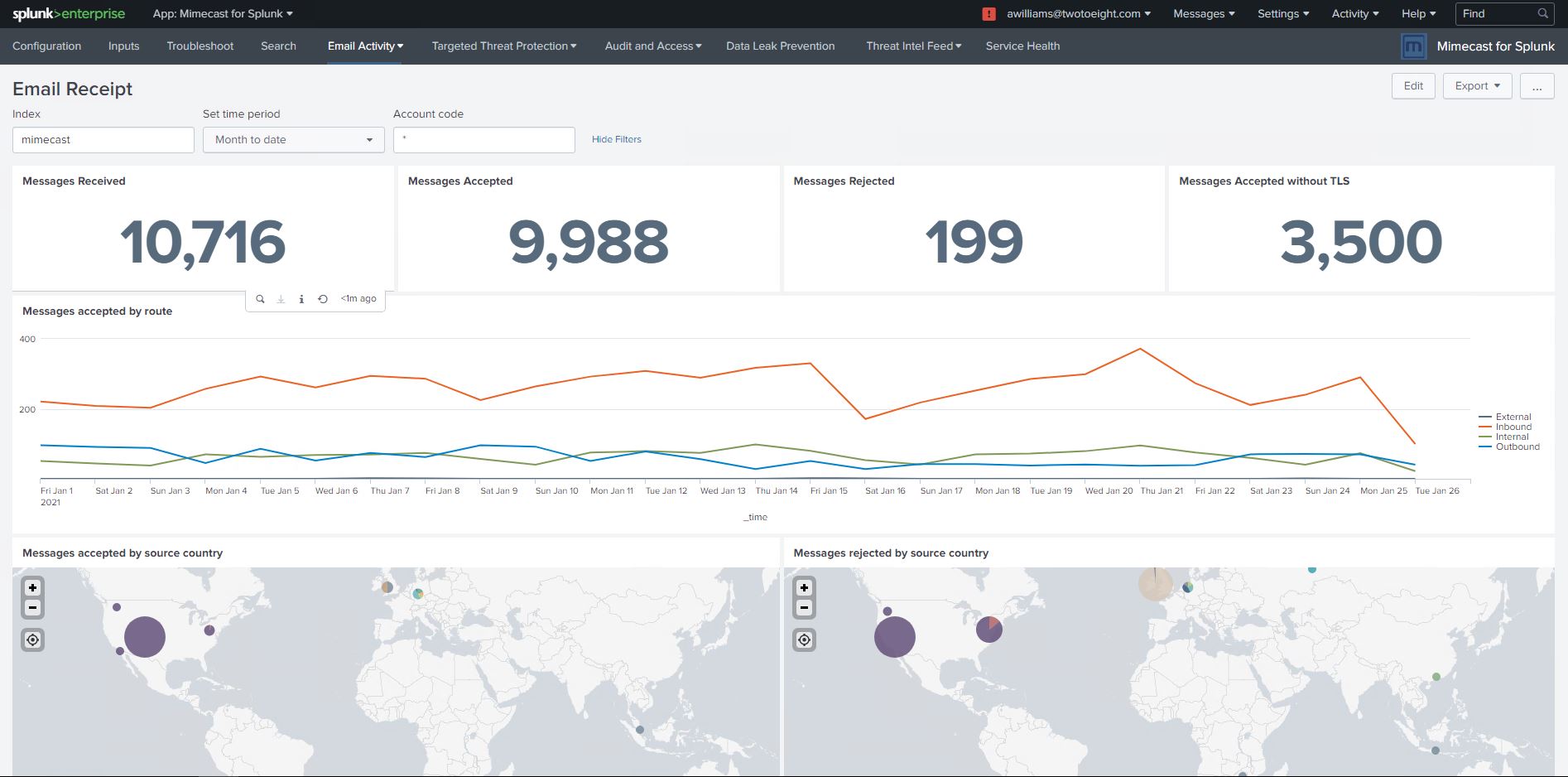
Mimecast + Splunk Use Cases:
- Threat correlation: Identify initial attack deployment methodology, characteristics, and subsequent access attempts without the need for manual effort or multiple toolsets.
- Advanced threat detection: Improve your organization’s security posture and detect threats by augmenting email perimeter defense with user and entity behavior analytics.
- Lateral movement detection: Detect and follow attackers even as they switch IP addresses, devices, or credentials.
- Alert prioritization: Increase efficiency and effectiveness by prioritizing the most pressing threats.
- Threat intelligence: Understand how your organization has been targeted and what attacks have been blocked for better protection at the email perimeter, inside the network and beyond its perimeter.
- Threat investigation: Analyze activity events before and after an attack across the entire attack chain to enhance analyst productivity and repair vulnerabilities.
